Understanding the Current Landscape: The Evolving Threat of Cyberattacks
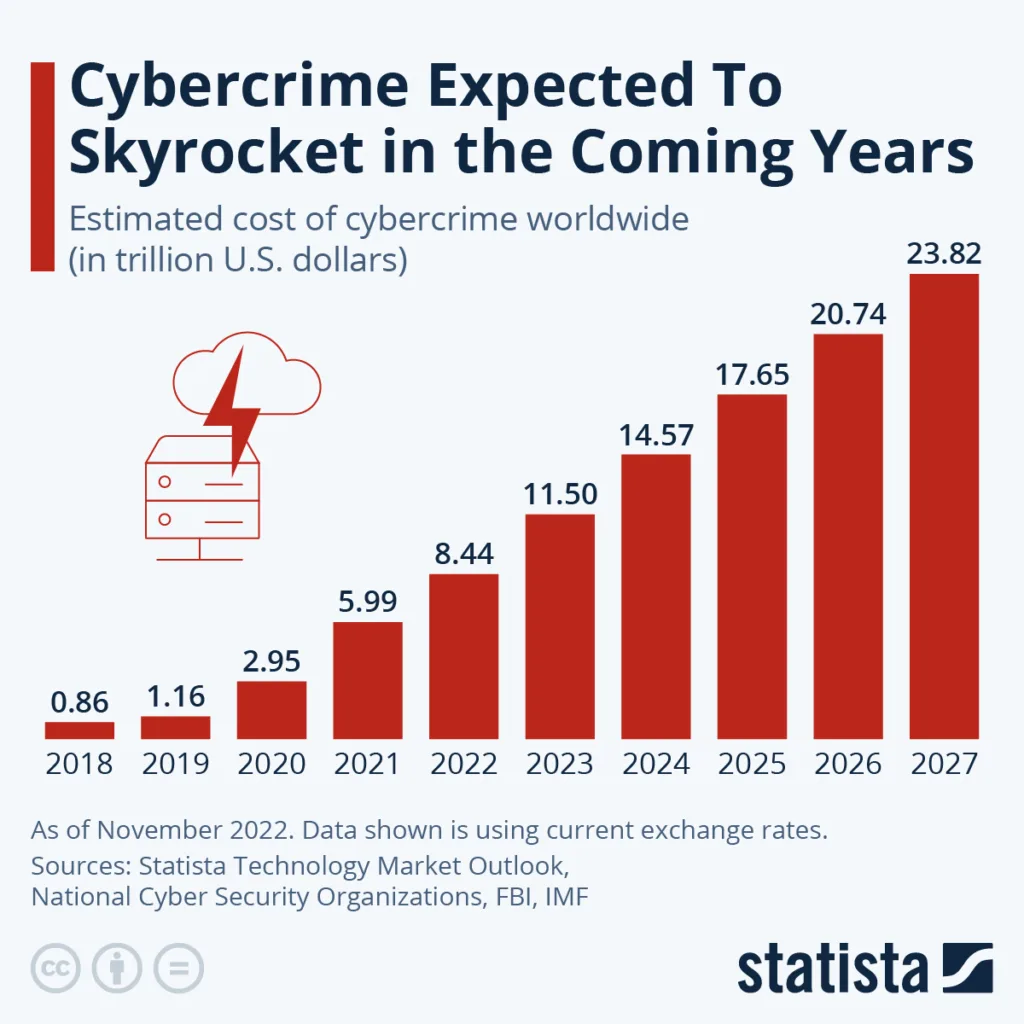
Cyberattacks have become increasingly prevalent in today's digital landscape, posing a significant threat to organizations of all sizes and industries. With advancements in technology and the growing reliance on interconnected systems, the threat of cyberattacks is evolving at an alarming rate. These attacks can range from simple phishing attempts to sophisticated ransomware campaigns, leaving businesses vulnerable to data breaches, financial losses, and reputational damage.
To illustrate the severity of this threat, let's consider a common cyberattack known as a distributed denial of service (DDoS) attack. In this type of attack, a malicious actor bombards a targeted website or network with a flood of incoming traffic, overwhelming the system's resources and rendering it inaccessible to legitimate users. For example, a popular online retailer could fall victim to a DDoS attack during a highly anticipated sale, causing the website to crash and resulting in significant revenue loss. Such attacks highlight the increasing need for organizations to implement robust security measures to protect their digital assets from the constant and evolving threat of cyberattacks.

Identifying the Most Common Cyberattacks Threatening Your Organization
One of the first steps in protecting your organization from cyber attacks is to identify the most common threats that you may encounter. By understanding the type of attacks that are prevalent in today's digital landscape, you can better prepare and implement effective security measures.
One common cyber attack is phishing, where attackers use fraudulent emails or messages to trick individuals into revealing sensitive information such as passwords or financial data. For example, an employee might receive an email claiming to be from their bank, asking them to click on a link and enter their login credentials. Unknowingly, the employee provides their information to the attacker, who can then gain unauthorized access to their account.
Another common cyber attack is malware, which refers to malicious software that is designed to infiltrate and damage computer systems. This can include viruses, worms, and Trojan horses, among others. For instance, a user might unknowingly download a file attachment from an untrusted source, which then installs malware onto their device. The malware can then disrupt operations, steal sensitive data, or even hold the system hostage until a ransom is paid.
These are just a couple of examples of common cyber attacks that organizations face. By being aware of the different types of threats that exist, you can take proactive steps to prevent them and safeguard your sensitive information.
Implementing a Strong Security Framework to Mitigate the Threat of Cyberattacks
Implementing a strong security framework is crucial to safeguarding your organization against the ever-growing threat of cyberattacks. A well-designed framework acts as a robust defense system that enables you to identify vulnerabilities, monitor for suspicious activities, and respond effectively to potential threats.
One of the key components of a strong security framework is the establishment of access controls. By implementing strict access controls, you can limit the exposure of sensitive data to only authorized individuals. For example, adopting a policy of least privilege ensures that employees only have access to the information necessary for their job roles, reducing the risk of unauthorized access and potential data breaches.
Another critical aspect of a strong security framework is the implementation of regular software updates and patches. Cybercriminals often exploit vulnerabilities in outdated software to gain unauthorized access to systems. By promptly applying software updates, you can mitigate these vulnerabilities and prevent cyberattacks.
For instance, regularly updating your operating systems, web browsers, and applications can protect your organization from known security flaws that have been fixed by software developers. Additionally, adopting automated update systems can streamline the process, ensuring that all devices and software within your network are consistently updated and protected from potential threats.
Training Your Team to Recognize and Respond to Cyber Threats
Training your team to recognize and respond to cyber threats is crucial in today's digital landscape. With the ever-evolving nature of cyberattacks, it is essential to equip your employees with the necessary knowledge and skills to identify and mitigate potential risks. By providing comprehensive cybersecurity training, you can empower your team to become the first line of defense against malicious activities.
One effective way to train your team is through interactive workshops and simulations. These hands-on activities allow employees to practice identifying and responding to various cyber threats in a controlled environment. For example, you can simulate a phishing attack by sending out a fake email and see how your team members react.
By experiencing these scenarios in a safe setting, they can learn to recognize suspicious emails, avoid clicking on malicious links, and report any potential threats promptly. Additionally, incorporating real-life examples of cyber incidents can help employees understand the consequences of their actions and the importance of maintaining a vigilant mindset.
Utilizing Advanced Security Tools to Counteract Cyberattacks
Utilizing advanced security tools is essential in today's digital landscape to counteract the ever-growing threat of cyberattacks. With the increasing sophistication of attacks, organizations need robust and proactive measures to protect their sensitive data and systems. These tools offer a range of capabilities, from real-time threat detection to vulnerability scanning, helping organizations stay one step ahead of cybercriminals.
One such tool is a next-generation firewall (NGFW), which goes beyond traditional firewalls in its ability to monitor and filter network traffic. By using deep packet inspection and application awareness, NGFWs can identify and block malicious traffic before it reaches the internal network.
For example, if an employee unknowingly clicks on a phishing email containing a malicious link, the NGFW can identify and block the connection to the compromised website or server. This prevents the malware from infiltrating the organization's systems and potentially causing serious damage.
Another advanced security tool that organizations can utilize is endpoint detection and response (EDR) software. EDR solutions provide real-time visibility into endpoints, such as laptops, desktops, and servers, allowing security teams to quickly detect and respond to threats.
EDR tools use advanced analytics and behavior-based algorithms to identify anomalous activities that may indicate a cyberattack. For instance, if an endpoint starts exhibiting unusual access patterns or accesses sensitive files without authorization, the EDR software can trigger an alert, enabling swift investigation and remediation.
By harnessing advanced security tools like NGFWs and EDR software, organizations can fortify their defenses against threat of cyberattacks. These tools, combined with other preventive measures, such as robust password policies and regular software patching, form a comprehensive security framework that helps mitigate the risks posed by cybercriminals.
However, it is important to note that advanced security tools are not a substitute for proper training and awareness among employees. Organizations must ensure that their teams are educated on cyber threats and best practices to effectively combat cyberattacks.
Creating a Response Plan for When Cyberattacks Occur
When it comes to cybersecurity, it's not a matter of if, but when a cyberattack will occur. As such, it is crucial for organizations to have a well-defined response plan in place to effectively mitigate the impact of these attacks. A response plan outlines the steps and procedures that need to be followed in the event of a cyberattack, ensuring a quick and coordinated response to minimize the damage.
The first step in creating a response plan is to establish clear communication channels. This includes defining the roles and responsibilities of each team member involved in the response process, as well as implementing a reliable method of communication, such as a dedicated incident response platform.
This ensures that information is shared swiftly and efficiently, enabling the team to take immediate action. Additionally, defining escalation paths can help streamline decision-making processes, ensuring that critical issues are addressed promptly.
Another crucial aspect of a response plan is the establishment of a containment strategy. This involves isolating and containing the affected systems to prevent further spread of the attack. By disconnecting compromised devices from the network and disabling compromised accounts or services, organizations can limit the attacker's ability to cause additional damage. Implementing this strategy may include temporarily shutting down affected systems or blocking suspicious network traffic to contain the attack. It is important to regularly test and update these containment measures to guarantee their effectiveness when a real cyberattack occurs.
Creating a comprehensive response plan plays a fundamental role in minimizing the impact of cyberattacks. It allows organizations to respond swiftly and efficiently, reducing downtime, financial losses, and potential damage to their reputation.
By establishing clear communication channels and implementing effective containment strategies, organizations can effectively navigate through the aftermath of a cyberattack, mitigating its consequences. In the face of constantly evolving threats, having a well-thought-out response plan in place is an essential component of a robust cybersecurity framework.
Ensuring Continuous Monitoring to Detect Threats Early
Continuous monitoring is essential in today's digital landscape to detect threats early and prevent potential cyberattacks. By constantly monitoring your network, systems, and applications, you can quickly identify any suspicious activities or vulnerabilities that may be exploited by hackers. Regular monitoring allows you to stay one step ahead of cybercriminals, reducing the risk of an attack and minimizing the potential damage it can cause.
An effective continuous monitoring strategy involves deploying security tools and technologies that provide real-time monitoring and alerting capabilities. These tools can automatically scan your network for any anomalies, such as unusual login attempts or data transfers, and immediately notify your cybersecurity team.
For example, intrusion detection systems (IDS) can monitor network traffic for any suspicious patterns, while security information and event management (SIEM) solutions can aggregate and analyze logs from various sources to identify potential threats. With these tools in place, you can proactively respond to incidents and take corrective actions before they escalate into full-blown attacks.
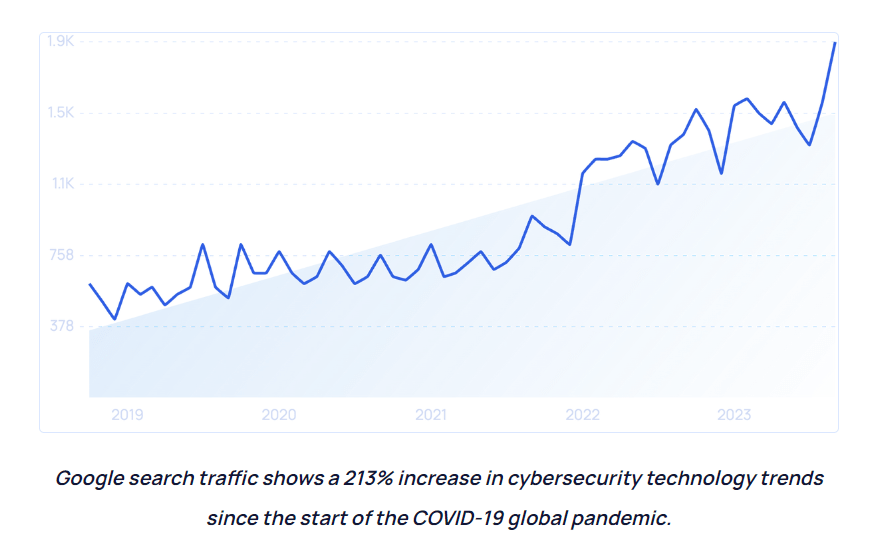
Staying Updated: Following Cybersecurity Trends to Foresee Potential Threats
As the threat landscape continues to evolve, staying updated on cybersecurity trends is crucial for organizations to foresee potential threat of cyberattacks. By following the latest developments in the field, businesses can enhance their security measures and proactively address vulnerabilities before they are exploited by cybercriminals.
One important trend to monitor is the increasing use of artificial intelligence (AI) and machine learning (ML) in cyberattacks. These technologies enable hackers to automate and personalize their attacks, making them more sophisticated and difficult to detect.
For example, AI-powered phishing attacks can mimic the communication styles of individuals within an organization, making it harder for employees to identify malicious emails. By staying informed about this trend, organizations can implement advanced email filtering tools and provide targeted training to educate their employees on recognizing and responding to such attacks.
Another trend that organizations should follow is the emergence of Internet of Things (IoT) devices and their impact on cybersecurity. With the growing number of interconnected devices, there is an increased attack surface for cybercriminals to exploit. For instance, insecure IoT devices can be compromised and used as entry points to launch attacks on the entire network. Therefore, staying updated on the security vulnerabilities associated with IoT devices and implementing strong security controls is essential to mitigate potential threats.
By staying updated on cybersecurity trends, organizations can anticipate and prepare for potential threat of cyberattacks. Whether it's keeping an eye on AI-driven attacks or understanding the risks posed by IoT devices, being aware of the latest developments allows businesses to stay one step ahead of cybercriminals.
Leveraging External Expertise to Evaluate Your Cybersecurity Measures
To ensure the effectiveness of your cybersecurity measures, it is crucial to leverage external expertise to evaluate your current strategies. External experts bring a fresh perspective and specialized knowledge that can help identify vulnerabilities or gaps in your security framework. By conducting thorough assessments, these experts can provide valuable insights and recommendations to enhance your cybersecurity defenses from threat of cyberattacks.
One way to leverage external expertise is through penetration testing. This involves simulating real-world cyberattacks to identify weaknesses in your systems and networks.
External experts, often referred to as ethical hackers, attempt to exploit vulnerabilities just as malicious actors would. This process helps uncover any potential entry points that hackers could use to gain unauthorized access. By conducting penetration tests regularly, you can proactively address vulnerabilities and strengthen your cybersecurity posture before an actual attack occurs.
Building a Culture of Security Awareness to Deter Cyber Threats
Building a Culture of Security Awareness to Deter Cyber Threats requires a comprehensive approach that involves educating employees about potential risks and encouraging responsible online behavior. By instilling a sense of vigilance among the workforce, organizations can create a collective defense against cyber threats.
One effective method is to conduct regular training sessions that cover topics such as identifying phishing emails, creating strong passwords, and recognizing suspicious online activities. For example, employees can be taught how to spot red flags in emails, such as unexpected attachments or requests for sensitive information. By providing real-life examples and practical tips, organizations can empower their employees to actively contribute to the security of the company's digital assets.
However, building a culture of security awareness goes beyond training sessions alone. It requires fostering an environment where cybersecurity is a shared responsibility from top to bottom. This can be achieved through clear communication channels and a supportive leadership approach. When leaders prioritize and demonstrate a commitment to cybersecurity, their actions set an example for others to follow. Regular reminders and updates about the latest threats and best practices can also help keep security awareness top of mind for employees. Additionally, incorporating security awareness into company policies and procedures, such as including it as part of new employee onboarding, ensures that all personnel are aware of their role in protecting against cyber threats.
What is a cyberattack?
A cyberattack is a malicious attempt to breach the security measures of a computer system or network to gain unauthorized access, steal data, disrupt operations, or cause damage.
Why is it important to understand the evolving threat of cyberattacks?
Understanding the evolving threat of cyberattacks helps organizations stay informed about the latest techniques used by hackers, enabling them to implement stronger security measures and protect against potential threats.
What are some common cyberattacks that organizations should be aware of?
Common cyberattacks include phishing, malware attacks, ransomware, DDoS attacks, and social engineering. Being aware of these threats helps organizations identify vulnerabilities and take necessary precautions.
How can organizations implement a strong security framework to mitigate cyberattacks?
Organizations can implement a strong security framework by conducting regular risk assessments, developing robust security policies and procedures, implementing access controls, and regularly updating and patching software and systems.
How can organizations train their teams to recognize and respond to cyber threats?
Organizations can train their teams by providing cybersecurity awareness training, conducting simulated phishing exercises, promoting a culture of security, and regularly communicating about new threats and best practices.
What advanced security tools can organizations use to counteract cyberattacks?
Advanced security tools include antivirus software, firewalls, intrusion detection systems, encryption tools, and security information and event management (SIEM) systems. These tools help detect and prevent cyberattacks.
Why is it important to have a response plan for when cyberattacks occur?
Having a response plan helps organizations respond quickly and effectively to minimize the impact of a cyberattack. It outlines the steps to be taken, responsibilities, communication channels, and recovery processes.
How does continuous monitoring help detect cyber threats early?
Continuous monitoring involves real-time monitoring of network traffic, system logs, and security events. By analyzing this data, organizations can identify and respond to potential threats proactively before they cause significant damage.
Why is it important to stay updated on cybersecurity trends?
Staying updated on cybersecurity trends helps organizations anticipate potential threats, understand emerging attack techniques, and implement preventive measures to safeguard their systems and data.
How can external expertise help evaluate an organization's cybersecurity measures?
External experts can conduct thorough security assessments and penetration tests to identify vulnerabilities and gaps in an organization's security measures. Their expertise can provide valuable insights for improving cybersecurity defenses.
How can organizations build a culture of security awareness to deter cyber threats?
Organizations can build a culture of security awareness by fostering a mindset of vigilance, promoting regular training and communication about cybersecurity, encouraging reporting of suspicious activities, and rewarding responsible security practices.